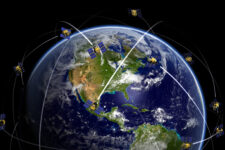
Threats

Making all-domain operations a warfighting capability means integrating, fusing, and disseminating a sensor picture appropriate for a particular theater segment, not all of them, says the Mitchell Institute’s David Deptula.
By Barry Rosenberg
While it’s comforting to imagine that US hardware will only be directed at terrorists and Iranian threats, “Bahrain’s history of suppressing internal dissent with external weaponry suggests that these choppers may end up serving a police function during times of crisis, as well.”
By Chyrine Mezher
Terrorist groups have evolved in the past two decades, some growing powerful enough that they are now seeking to transform into political actors.
By Riad Kahwaji
America’s allies in the Middle East are weighing options to avoid meeting the fate of the Afghani government, as regional scholars talk of the post Pax Americana era.
By Riad Kahwaji
Hezbollah continues to develop its arsenal with a continued focus on precision guided munitions, and both Israel and Hezbollah watch for any change in the rules of engagements along the Blue Line.
By Chyrine Mezher
The opening of the base signifies Egypt’s determination to assert itself as a regional naval power with vast capacities and challenge efforts by its competitors like Turkey to expand their area of influence and control oil and gas rich zones of the Mediterranean.
By Chyrine Mezher
“So what will happen is you’ll be destroying your grandmother’s computer in Kansas that has been taken over,” cyber policy expert Herb Lin said. “It’s not clear to me that that’s the best way.”
By Brad D. Williams
“Believe it or not, we found that the primary barriers to being able to field the software tools are bureaucratic, said Heather Penney of the Mitchell Institute.
By Colin Clark
“The PRC’s pattern of irresponsible behavior in cyberspace is inconsistent with its stated objective of being seen as a responsible leader in the world,” a senior administration official said on Sunday night.
By Brad D. Williams
It is more of a repositioning rather than a withdrawal and “does not reflect any political orientation similar to the one to withdraw troops from Afghanistan,” strategic expert and political researcher Abdullah Al Jenaid tells Breaking Defense.
By Chyrine Mezher
The test involved electronic attack efforts against radars while previous tests had been directed against the communications systems binding IBCS to its sensors.
By Colin Clark
“CISA has validated various proofs of concept and is concerned that exploitation of this vulnerability may lead to full system compromise of agency networks if left unmitigated,” the emergency directive says.
By Brad D. Williams
The Security Measures publication focuses on running software, while the Recommended Minimum Standards focuses on developing it.
By Brad D. Williams